- SMS blaster -Svindel is increasing and they are difficult to detect
- These scams involve cyber criminals running around cities and targeting nearby phones with fake cell towers
- There are a few simple ways to protect yourself from these scams
The term ‘SMS Blaster’ is still unknown to many, but these devices are increasingly popular weapons used by cyber criminals – and your phone may be the target.
These small devices can be used to target hundreds of phones at a time, and they have been caught and send as many as 100,000 text messages per hour. The worst thing is that you may not even notice if you were targeted by an SMS blaster attack.
Fortunately, you can protect yourself from these attacks with a simple frame on Android. IPhone users are less fortunate, but there are ways to stay sure no matter what smartphone you are using.
How does SMS Blaster Scams work?
The term ‘SMS blaster’ refers to small, portable devices that scammers can fit into the trunk of a car or even in a backpack.
These devices mimic cell towers and fool phones to connect by sending out a false signal and then using this opening to send hundreds or even thousands of phishing texts (a practice known as ‘Smishing’).
In reality, a SMS blaster is a rather modest unit, and those found with them are often hired by cyber criminals for the sole purpose of driving around in certain areas. As the security company Sekoia (via ARS Technica) recently reported, scammers have also utilized unsecured cellular routers typically used in industrial environment to fire phishing messages.
As described by CableSo-called SMS blasters force uncertain connections by creating an illegitimate phone mast, called a cell side simulator (CSS). Phones caught in its radius – which can be up to 1,000 meters (328 feet) according to the Swiss national cybersecurity center (NCSC) – are vulnerable to SMS fraud.

The device is initially connected to nearby phones by sending a 4G signal. Then it pushes them to down adjusting to 2G, which is much less safe.
“The 2G fake base station is then used to send (explosion) malicious SMSEs to the mobile phones originally caught by 4G False Base Station,” Cathal McDAID, VP for technology and telecommunications at Enea, told Wired. The whole process, from the initial connection to sending a text, can take less than 10 seconds.
The actual messages often contain phishing -links and they are not blocked by network operators. Regardless of the carrier and whether you are using an older phone or one of Best smartphonesCan you be vulnerable to SMS blaster attacks.
The worst part of these scams is that cyber criminals don’t even need to know your phone number.
SMS blaster -attacks are still more common
Wired reports that these scams originate from Southeast Asian countries, but they are now increasingly common worldwide.
Just a few months ago a man in the UK was jailed for more than a year to use a SMS blaster in the trunk of his car (via The Guardian). He drove around London for a few days in March 2025, and the lyrics he sent out reached thousands of potential victims. Ironically, when authorities came to arrest him, they received a text that claimed to be from HM revenue and customs -the result of the Phishing device.

With that said, this technique is still relatively new and mobile networks are helpless when it comes to stopping them. “None of our security checks apply to the messages that phones receive from them,” Anton Reynaldo Bonifacio, head of information security and boss AI officer at Globe Telecom told Wired.
SMS blasters are sold online for thousands of dollars, which for a group of cyber criminals is not much of an obstacle. So far, there have been reports of SMS blaster fraud from many countries, including New Zealand, Brazil, Vietnam, Thailand, Japan and the UK.
How to protect yourself
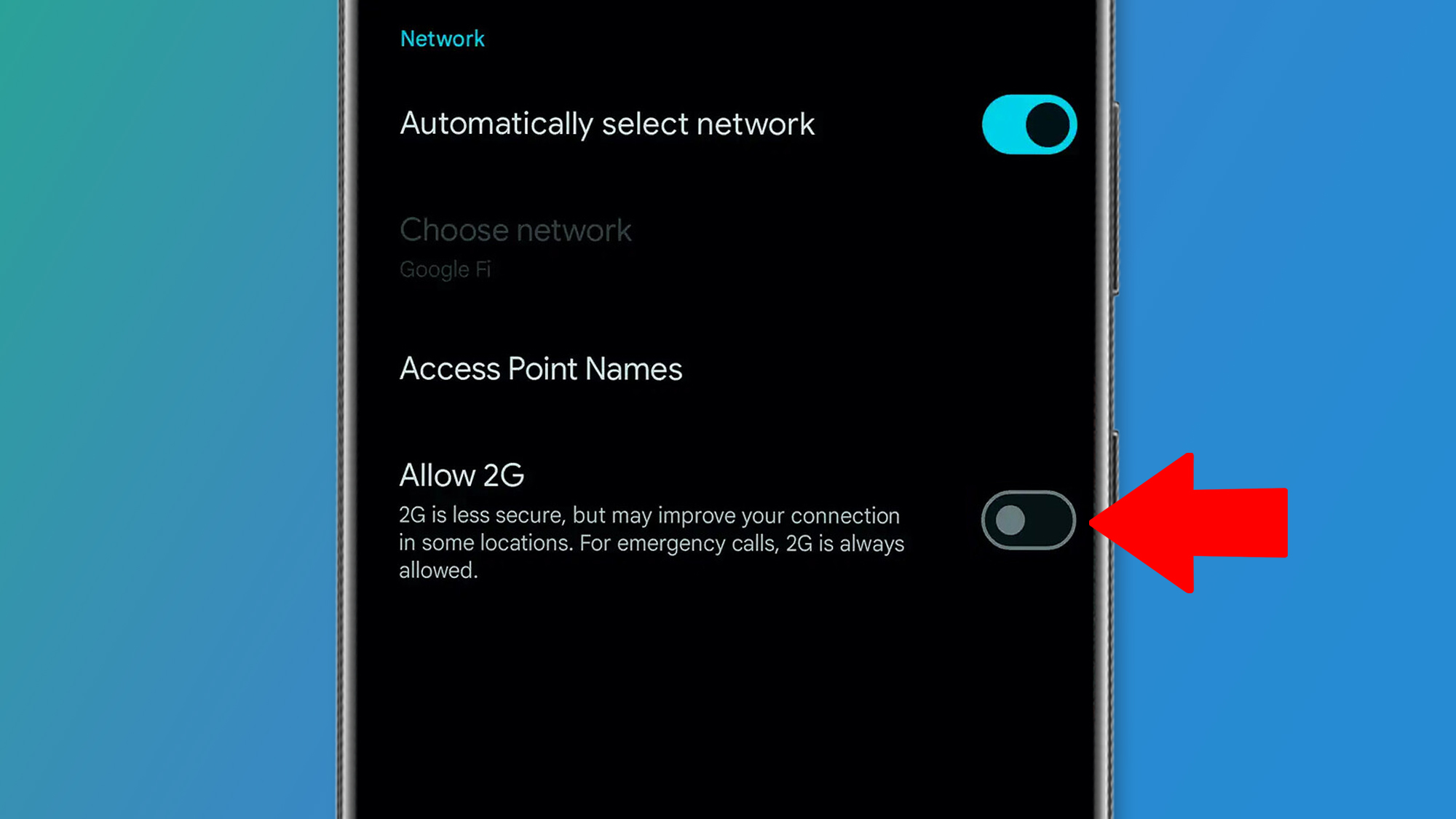
If you have an Android phone running Android 16 or newer, you can disable 2G connection on your device.
To turn off the 2G connection, look for the “2G Network Protection” frame in your mobile network or SIM settings. This can typically be found in Settings> Network and Internet> Sims, where you can find a ‘Allow 2G’ -tgle (see below).
On Samsung phones, look for a similar setting in Settings> Connections> Mobile Network, where there must be a ‘Allow 2G Service’ train. In addition to the introduced Android 16 also a change that Flag fake cell towers and warn you About them.
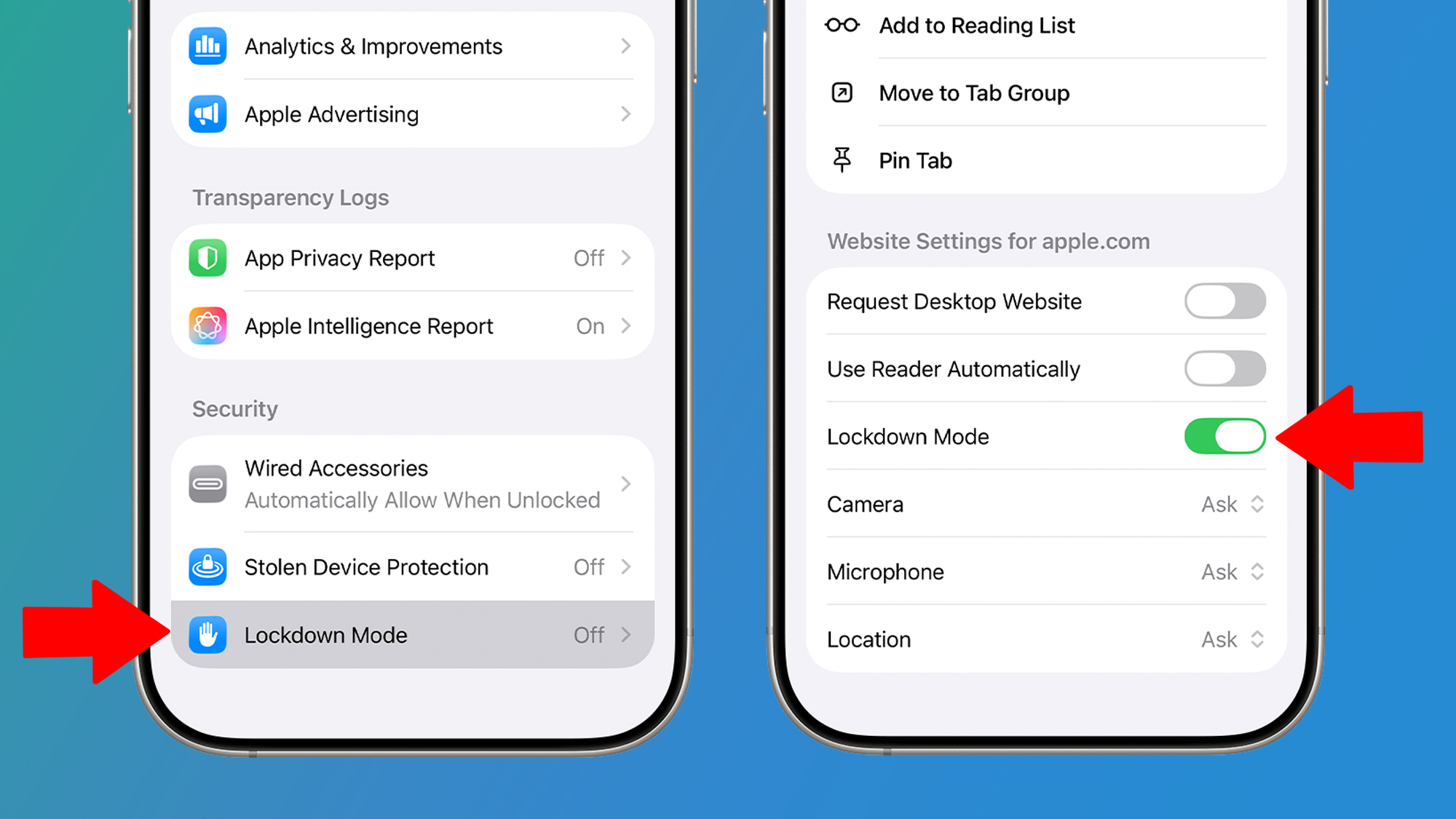
Apple does not have an exact equivalent with this, which makes it a little harder to avoid 2G networks – but not quite impossible. IPhone’s Lockdown mode (below, available on iOS 16 or newer) disables 2G connections, but you also lose many other features along with it, so regular use is not really recommended.
To find it on your iPhone, go to Settings> Privacy and Security, and then press Lockdown mode. This option is also available on iPads using the same process.
Whether you are using Android or iOS, the wider advice on avoiding SMS fraud is the same regardless of source.
Pay particular attention to texts that ask you to pay – for example, a toll. Other favorites among scammers are texts about deliveries, late payments or refund, so never follow these messages without first examining them.
There are some other narrative characters. Fidus texts often have grammatical errors or disagreements with formatting. Pause for a moment and also take a closer look at any URLs as they often contain oddities or gifts.
Of course, you should also only log in to your bank app or delivery service directly from your own address book or bookmarks (or by manually typing it in a browser) instead of clicking any links in text messages.
Follow Techradar on Google News and Add us as a preferred source To get our expert news, reviews and meaning in your feeds. Be sure to click the Follow button!
And of course you can too Follow Techradar at Tiktok For news, reviews, unboxings in video form and get regular updates from us at WhatsApp also.



