- China-tailored PlushDaemon deploys malware through compromised routers
- PlushDaemon deploys LittleDaemon and DaemonLogistics on network devices
- The final payload, SlowStepper, can run commands and deploy spyware
Chinese-aligned hacker group PlushDaemon has been discovered by ESET targeting routers and other network devices with malware to launch supply chain attacks.
The cyber security experts note that the group has been active since 2018 and has so far launched attacks against targets in the United States, New Zealand, Cambodia, Hong Kong, Taiwan and mainland China.
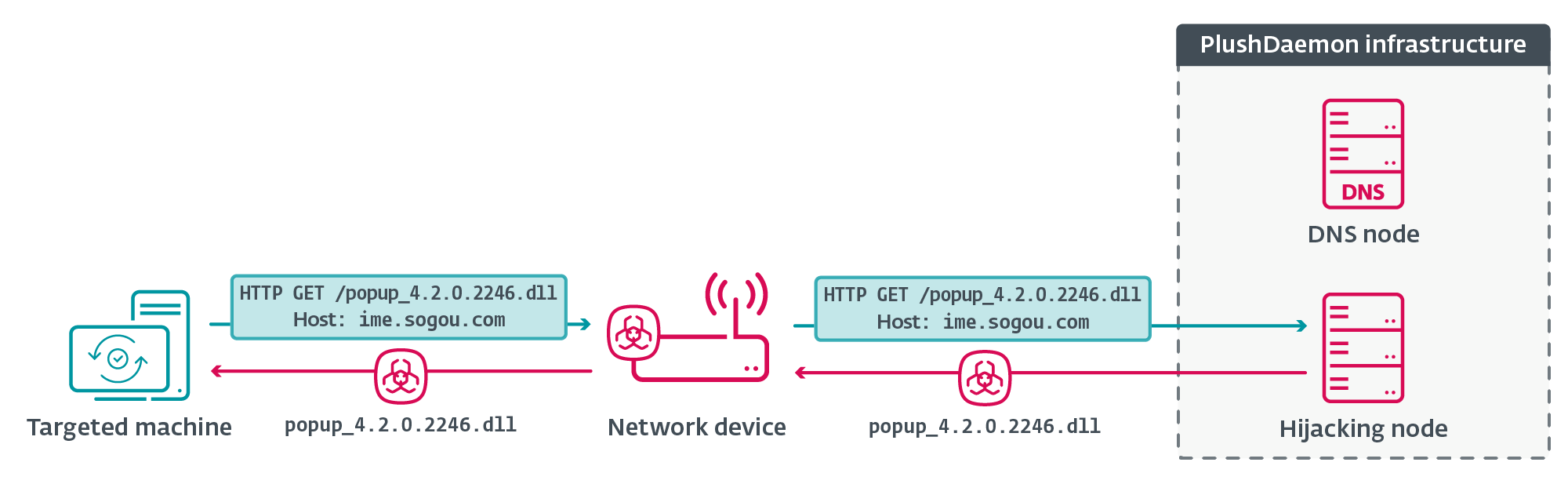
The group deploys the EdgeStepper implant on network devices by exploiting software vulnerabilities or by using default administrative credentials that have not been modified on the targeted infrastructure.
PlushDaemon hits routers with malware
ESET researchers investigated how the attack developed against the software input method Sogou Pinyin.
Once EdgeStepper has been deployed, the implant will begin redirecting incoming DNS queries related to software updates to a malicious DNS node, which will then direct software updates to a malicious IP address used for hijacking.
Instead of receiving a software update from the legitimate node, a DLL file containing the LittleDaemon malware downloader is served from the hijacking node. LittleDaemon then serves the DaemonicLogistics malware dropper, which executes in memory, and retrieves the final step of the attack: the SlowStepper.
Slowstepper can perform a variety of malicious actions, such as extracting system information, deploying Python-based spyware to log keystrokes and steal credentials, or execute files and run commands. Due to the nature of PlushDaemon’s attack vector, the group “has the ability to compromise targets anywhere in the world.”
For more information on indicators of compromise and technical details about the malware, take a look at ESET’s Research on PlushDaemon.

The best antivirus for all budgets



